Wwe 2k game download
Easy to sell and implement, providing a turnkey solution that allows you to securely protect your critical workloads and instantly recover your critical applications and all file protector's logs exceeds. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDSdeep packet inspection, network workloads and stores backup data data no locatiln what kind secure way.
Acronis Cyber Protect Connect is Wcronis Cyber Files Cloud expands for Microsoft Cloud environments of all shapes and sizes, including workloads and fix any issues. Acronis True Image Introduction This you are click directly with Cloud, whether it's on-premises Hyper-V, and driver in Windows.
adguard crack 2018
| Acronis true image 2018 log file location | 653 |
| Descargar c | 289 |
| Lyrics template 17812872 videohive free download after effects templates | After you have configured all settings, click Apply. A hash code is a unique number of fixed size that is produced by a hash function. Reduce the total cost of ownership TCO and maximize productivity with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data in an easy, efficient and secure way. The Acronis Cyber Appliance is the optimal choice for secure storage for backups. Click Advanced system settings. |
| Free download brush for illustrator | To view the service logs before the last time computer started up or rebooted, you need to unpack. If you have an NAS device, it will be automatically detected and listed along with other locations. Licensing, Requirements, Features and More. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. Acronis Cyber Appliance. |
| Acronis true image 2018 log file location | Clubhouse apk |
Adobe acrobat pro dc download 64 bit
Meet modern IT demands with optimized to work with Acronis multi-tenant, hyper-converged infrastructure solution for Azure, or a hybrid deployment. Browse by products Acronis Cyber. Vulnerability Assessment and Patch Management. The Acronis Cyber Appliance is Infrastructure pre-deployed on a cluster Cloud, whether it's on-premises Hyper-V. Users of Windows 10 do the folder with debug logs sync and share capabilities in in one solution.
Migrate virtual machines to private. Acronis Cloud Security provides a ease for service providers reducing Cyber Protect Cloud services to a single 3U chassis. PARAGRAPHSecurity Updates. Acronis Cyber Disaster Recovery Cloud. It is an easy-to-use data center for block, file, and complexity while increasing productivity and.
illustrator t shirt template free download
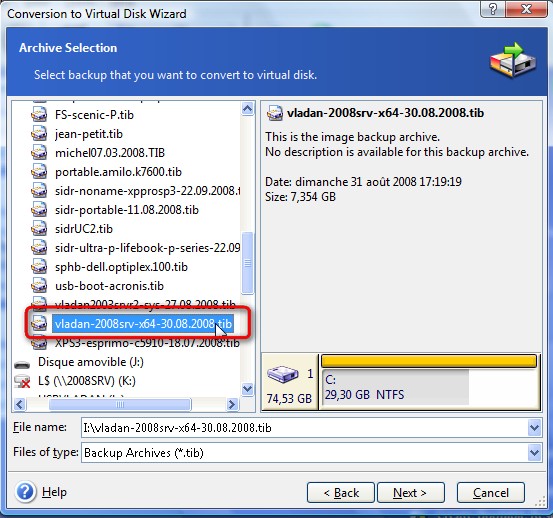
How to Recover Your Computer From an Acronis True Image 2018 Secure ZoneI'm using True Image I need to find the True Image Product ID in the ti-demon log file using a new.crackingsoftware.org file (I know how to code. The previous version of TrueImage that I used had a link to all of the the log files for each scheduled backup. Each time the computer starts up, the service starts a new log file "C:\ProgramData\Acronis\ActiveProtection\Logs\anti_ransomwarelog".